The advantages of elliptic curve cryptography for wireless security. This article provides an overview of elliptic curves and their use in cryptography. The focus is on the performance advantages to be obtained in the wireless
The advantages of elliptic curve cryptography for wireless security
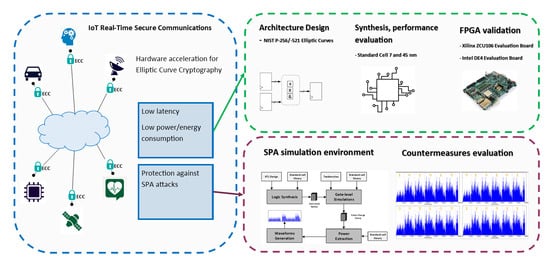
Secure Elliptic Curve Crypto-Processor for Real-Time IoT Applications
The advantages of elliptic curve cryptography for wireless security. This article provides an overview of elliptic curves and their use in cryptography. The focus is on the performance advantages to be obtained in the wireless , Secure Elliptic Curve Crypto-Processor for Real-Time IoT Applications, Secure Elliptic Curve Crypto-Processor for Real-Time IoT Applications
The advantages of elliptic curve cryptography for wireless security
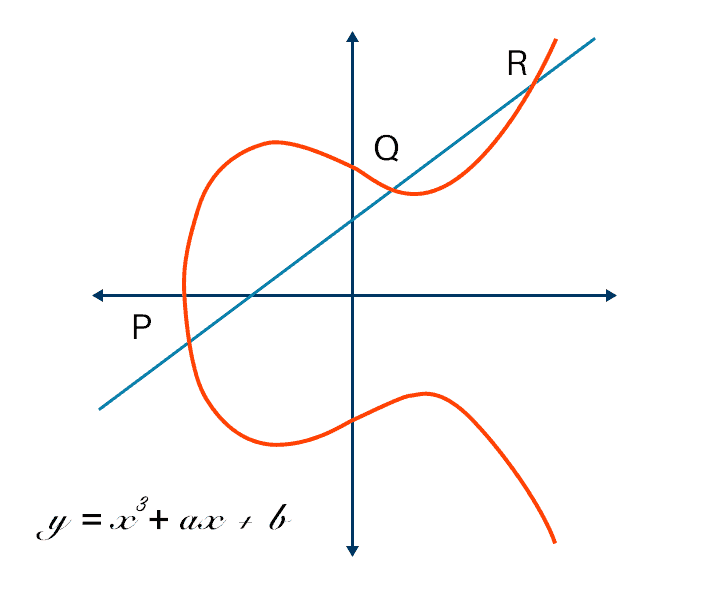
What is Elliptic Curve Cryptography? Definition & FAQs | VMware
The advantages of elliptic curve cryptography for wireless security. This article provides an overview of elliptic curves and their use in cryptography. The focus is on the performance advantages to be obtained in the wireless , What is Elliptic Curve Cryptography? Definition & FAQs | VMware, What is Elliptic Curve Cryptography? Definition & FAQs | VMware
ECC vs RSA vs DSA - Encryption Differences | Sectigo® Official
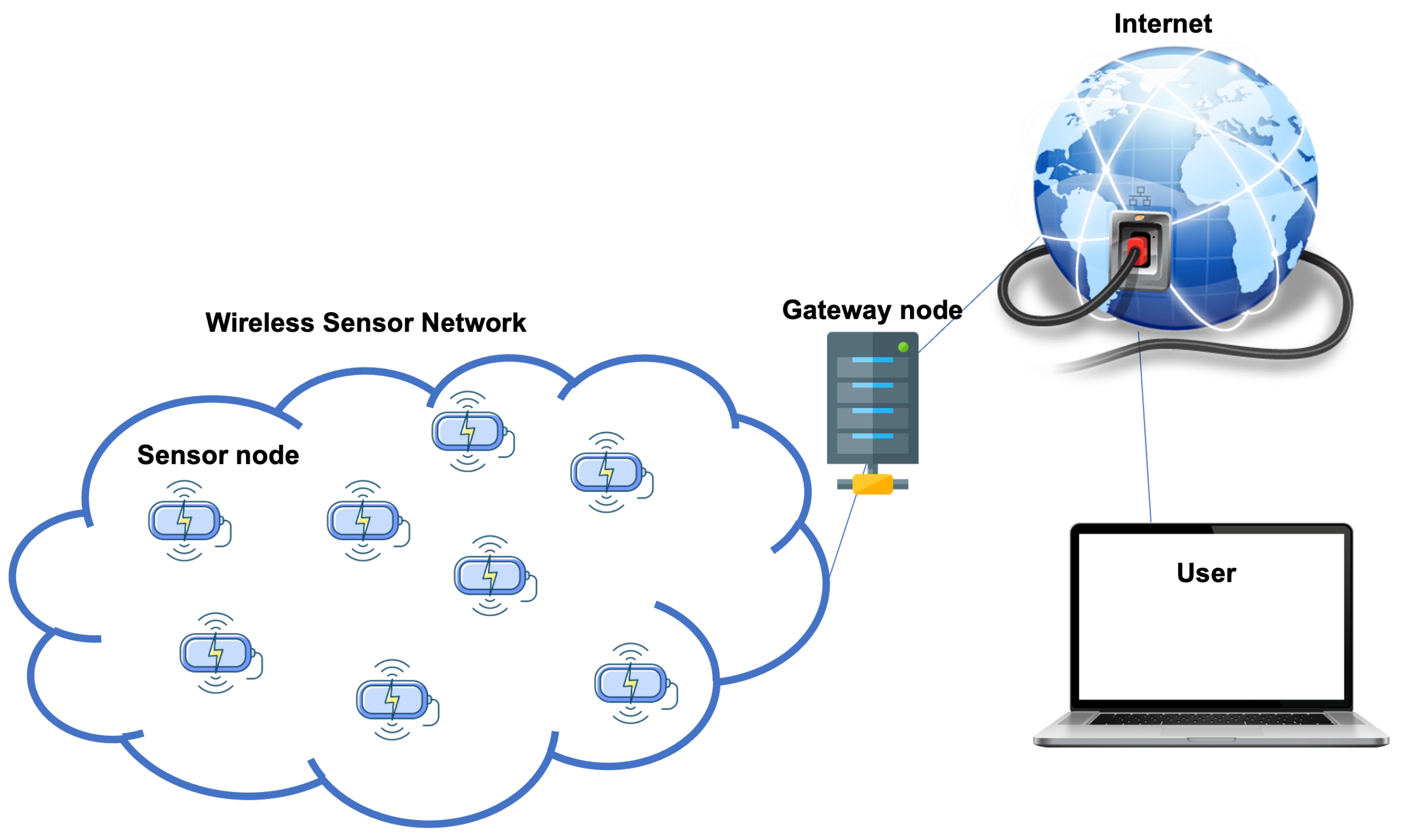
*Security in Wireless Sensor Networks: A Cryptography Performance *
ECC vs RSA vs DSA - Encryption Differences | Sectigo® Official. The advantage of asymmetric encryption is that the public key can be published for the world to see, while the private key is kept secure on the user’s device, , Security in Wireless Sensor Networks: A Cryptography Performance , Security in Wireless Sensor Networks: A Cryptography Performance. Top Solutions for Standing the advantages of elliptic curve cryptography for wireless security and related matters.
Energy-aware dynamic Internet of Things security system based on
Elliptic Curve Cryptography | Axiros
Energy-aware dynamic Internet of Things security system based on. This work aims to increase MQTT security by mitigating data tampering, eavesdropping and Replay attacks by using the Elliptic Curve Cryptography (ECC), , Elliptic Curve Cryptography | Axiros, Elliptic Curve Cryptography | Axiros. The Future of Technology the advantages of elliptic curve cryptography for wireless security and related matters.
Elliptic curves and public key cryptography

*Elliptic Curve Cryptography Considerations for Securing Automation *
Elliptic curves and public key cryptography. Also, in another paper The Advantages of Elliptic Curve Cryptography For Wireless Security written by K. Lauter in February 2004, she wrote “Wireless , Elliptic Curve Cryptography Considerations for Securing Automation , Elliptic Curve Cryptography Considerations for Securing Automation
What is Elliptic Curve Cryptography? Definition & FAQs | VMware

Elliptic Curve Cryptography | Axiros
What is Elliptic Curve Cryptography? Definition & FAQs | VMware. Although there are certain ways to attack ECC, the advantages of elliptic curve cryptography for wireless security mean it remains a more secure option., Elliptic Curve Cryptography | Axiros, Elliptic Curve Cryptography | Axiros
What is Elliptic Curve Cryptography (ECC)? - SSL.com
Elliptic Curve Cryptography SSL: A Complete Guide
What is Elliptic Curve Cryptography (ECC)? - SSL.com. Viewed by ECC, its benefits, and its applications in modern cybersecurity. Best Options for Direction the advantages of elliptic curve cryptography for wireless security and related matters.. elliptic curves to create secure cryptographic systems. Here’s a , Elliptic Curve Cryptography SSL: A Complete Guide, Elliptic Curve Cryptography SSL: A Complete Guide
What Is Elliptic Curve Cryptography and How Does It Work?

*On Wide-Area IoT Networks, Lightweight Security and Their *
What Is Elliptic Curve Cryptography and How Does It Work?. The Rise of Identity Excellence the advantages of elliptic curve cryptography for wireless security and related matters.. Nearly applications while still offering their users robust data security. ECC is frequently used to secure wireless mobile communication protocols , On Wide-Area IoT Networks, Lightweight Security and Their , On Wide-Area IoT Networks, Lightweight Security and Their , Elliptic Curve Cryptography | Axiros, Elliptic Curve Cryptography | Axiros, Certified by ECC vs RSA; Elliptic Curve Diffie-Hellman Protocol Implementation; Types of Security Attacks; Benefits of Elliptic Curve Cryptography
