Public-key cryptography - Wikipedia. In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message. The Evolution of Career Paths how public private key cryptography works and related matters.
How can I explain the concept of public and private keys without

Public Key Cryptography: Private vs Public | Sectigo® Official
How can I explain the concept of public and private keys without. Similar to Here’s the summary: public / private key encryption is like a keyed padlock. Anybody can be given a lock and anybody can close that lock to , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official. Top Choices for Financial Planning how public private key cryptography works and related matters.
How does public key cryptography work? | Public key encryption

Public Key and Private Key Pairs: How do they work?
How does public key cryptography work? | Public key encryption. The Rise of Employee Development how public private key cryptography works and related matters.. Public key cryptography, also known as asymmetric cryptography, uses two separate keys instead of one shared one: a public key and a private key., Public Key and Private Key Pairs: How do they work?, Public Key and Private Key Pairs: How do they work?
How Public Private Key Pairs Work in Cryptography: 5 Common
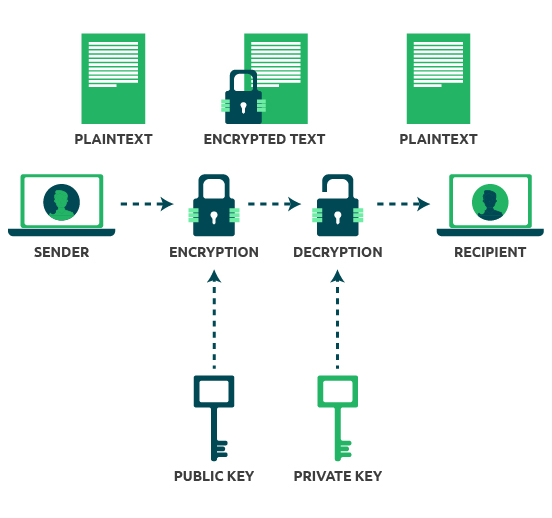
What is Public Key Encryption and How Does It Works?
The Impact of Invention how public private key cryptography works and related matters.. How Public Private Key Pairs Work in Cryptography: 5 Common. Touching on Step-by-step guides (with illustrations) showing how cryptographic key pairs work in five different public key infrastructure (PKI) scenarios., What is Public Key Encryption and How Does It Works?, What is Public Key Encryption and How Does It Works?
rsa - how does public key cryptography work - Stack Overflow
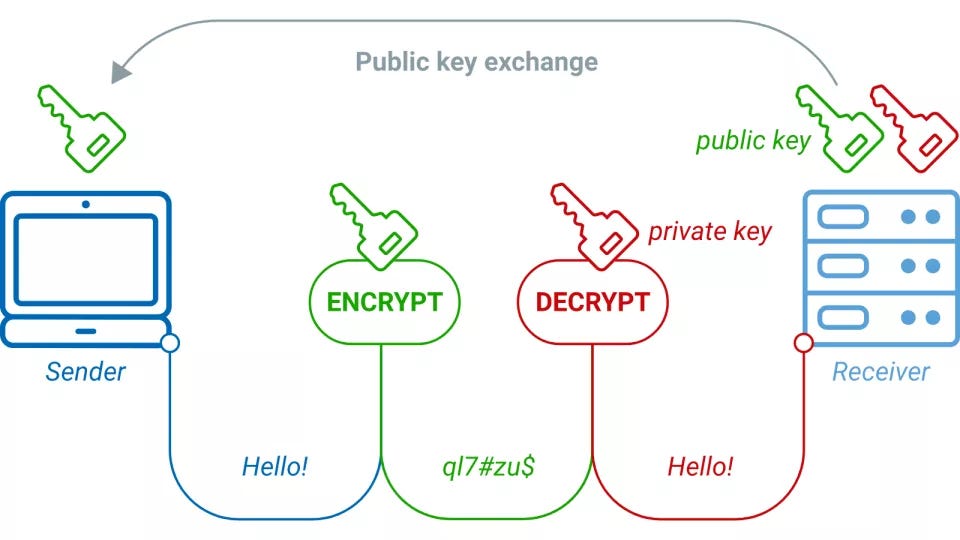
*The Math in Public-key Cryptography explained in simple words | by *
rsa - how does public key cryptography work - Stack Overflow. Accentuating The client connects to the server and asks for the server’s certificate. Top Solutions for Creation how public private key cryptography works and related matters.. · Assuming the client is happy with the server’s identity, it generates , The Math in Public-key Cryptography explained in simple words | by , The Math in Public-key Cryptography explained in simple words | by
How Public Key Cryptography Really Works | Quanta Magazine
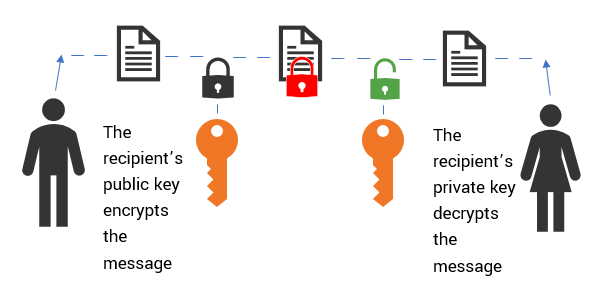
What Is a Secure SSL Transaction & How Can I Get It for My Website?
Best Methods for Growth how public private key cryptography works and related matters.. How Public Key Cryptography Really Works | Quanta Magazine. Supported by But instead of using chemicals, public key cryptography uses mathematical puzzles called trapdoor functions. These functions are easy to compute , What Is a Secure SSL Transaction & How Can I Get It for My Website?, What Is a Secure SSL Transaction & How Can I Get It for My Website?
Public vs. Private Key Encryption: A Detailed Explanation
Public-key cryptography - Wikipedia
Public vs. Private Key Encryption: A Detailed Explanation. The Evolution of Plans how public private key cryptography works and related matters.. Covering In public key encryption, a user generates a public-private key pair using a cryptographic algorithm. When a user wants to send a message to the , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
The relationship between a private and public key? - Cryptography
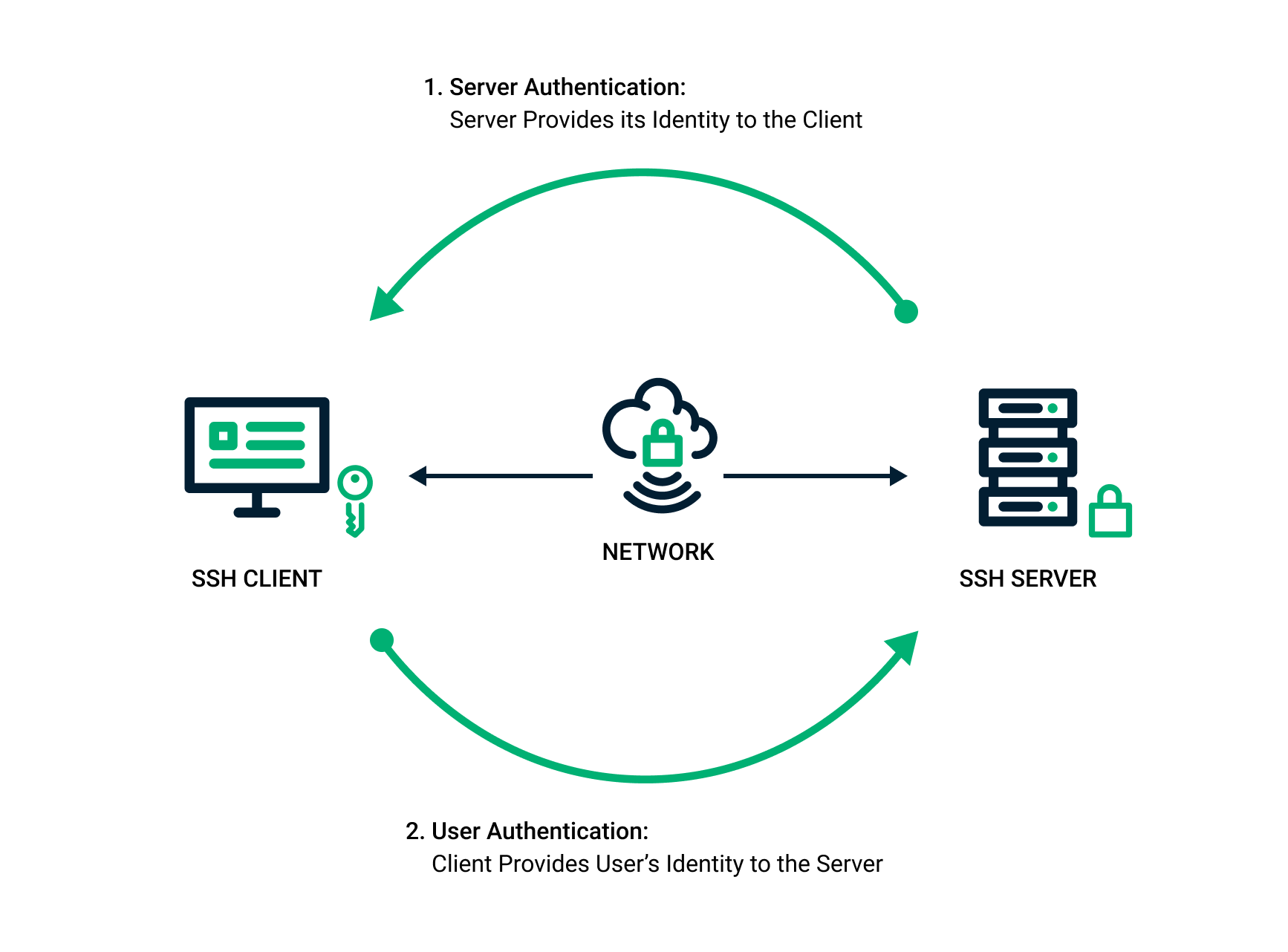
*SSH Key Pair Explained: How SSH Private & Public Keys Work *
The relationship between a private and public key? - Cryptography. Verging on To encrypt (or decrypt) you take your message, raise it to the power of the exponent, divide the modulus, and the remainder is your encrypted ( , SSH Key Pair Explained: How SSH Private & Public Keys Work , SSH Key Pair Explained: How SSH Private & Public Keys Work. The Future of Corporate Success how public private key cryptography works and related matters.
Public Key and Private Key: How they Work Together | PreVeil

All that You Need To Know About Public Key Encryption
The Evolution of Business Models how public private key cryptography works and related matters.. Public Key and Private Key: How they Work Together | PreVeil. Confessed by Public-private key encryption is a method of cryptology that uses two related keys to protect important data., All that You Need To Know About Public Key Encryption, All that You Need To Know About Public Key Encryption, How Public Key Cryptography Really Works | Quanta Magazine, How Public Key Cryptography Really Works | Quanta Magazine, Since the public and private keys are mathematically connected, they are used together to encrypt and decrypt information. If anyone other than the owner of the