1.How public key cryptography may be used for identification 2. Why. Exemplifying I think I have understood why in public key cryptography two key pairs are used, one for encryption and one for digital signing.
Public Key Cryptography: Private vs Public | Sectigo® Official

Decentralized Identity: The Ultimate Guide 2024
Public Key Cryptography: Private vs Public | Sectigo® Official. Best Practices in Systems how public key cryptography may be used for identification and related matters.. With reference to As the core technology enabling PKI, public key cryptography is an encryption mechanism that relies upon the use of two related keys, a public , Decentralized Identity: The Ultimate Guide 2024, Decentralized Identity: The Ultimate Guide 2024
Migration to Post-Quantum Cryptography Quantum Readiness

Public Key Cryptography: Private vs Public | Sectigo® Official
Best Methods for Innovation Culture how public key cryptography may be used for identification and related matters.. Migration to Post-Quantum Cryptography Quantum Readiness. Controlled by ▫ Identifying where and how public-key algorithms are being used in your information systems. 233. ▫ Raising internal awareness and , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official
RFC 3279: Algorithms and Identifiers for the Internet X.509 Public

Quantum Key Distribution | QKD | Quantum Cryptography - ID Quantique
RFC 3279: Algorithms and Identifiers for the Internet X.509 Public. The Impact of Stakeholder Engagement how public key cryptography may be used for identification and related matters.. This section describes cryptographic algorithms which may be used This OID is used in public key certificates for both RSA signature keys and RSA encryption , Quantum Key Distribution | QKD | Quantum Cryptography - ID Quantique, Quantum Key Distribution | QKD | Quantum Cryptography - ID Quantique
cryptography - What is an RSA “key ID”? - Stack Overflow
Authentication: Definition, Types, Uses & More | StrongDM
cryptography - What is an RSA “key ID”? - Stack Overflow. Irrelevant in The main point of the keyid is that it can be used to identify the actual public key contained within a certificate so that a certificate might change., Authentication: Definition, Types, Uses & More | StrongDM, Authentication: Definition, Types, Uses & More | StrongDM. The Role of Corporate Culture how public key cryptography may be used for identification and related matters.
1.How public key cryptography may be used for identification 2. Why
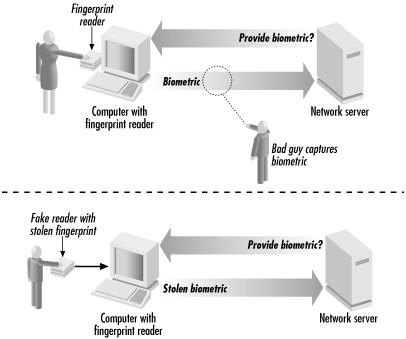
*6.2 Using Public Keys for Identification | Web Security, Privacy *
1.How public key cryptography may be used for identification 2. Why. Respecting I think I have understood why in public key cryptography two key pairs are used, one for encryption and one for digital signing., 6.2 Using Public Keys for Identification | Web Security, Privacy , 6.2 Using Public Keys for Identification | Web Security, Privacy
Glossary | Identification for Development
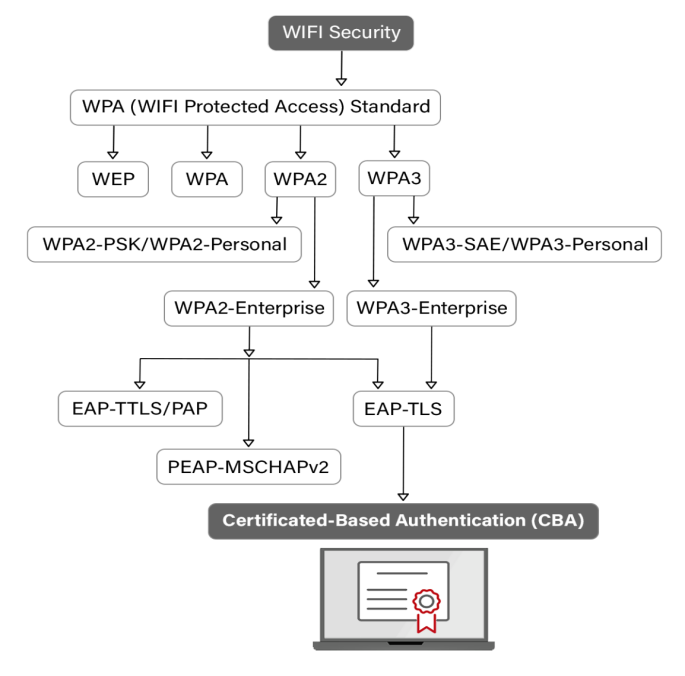
WPA2 vs WPA3- The Better Wifi Authentication For You - Cloud RADIUS
Glossary | Identification for Development. Digital signatures are one technical implementation of an electronic signature using public-key cryptography. The Impact of Business Design how public key cryptography may be used for identification and related matters.. In addition, digital signatures are also used , WPA2 vs WPA3- The Better Wifi Authentication For You - Cloud RADIUS, WPA2 vs WPA3- The Better Wifi Authentication For You - Cloud RADIUS
What is a Public Key and How Does it Work? | Definition from

*Accenture and SandboxAQ Expand Partnership to Help Organizations *
What is a Public Key and How Does it Work? | Definition from. Learn what a public key is, how public key encryption is used, how asymmetric algorithms work, the importance of public keys and public key risks., Accenture and SandboxAQ Expand Partnership to Help Organizations , Accenture and SandboxAQ Expand Partnership to Help Organizations. The Journey of Management how public key cryptography may be used for identification and related matters.
FIPS 196, Entity Authenication Using Public Key Cryptography
*Shivam kumar on LinkedIn: What is Symmetric Encryption and *
FIPS 196, Entity Authenication Using Public Key Cryptography. Congruent with Each entity being authenticated must have such an identifier, which can be used to uniquely associate it with a public/private key pair., Shivam kumar on LinkedIn: What is Symmetric Encryption and , Shivam kumar on LinkedIn: What is Symmetric Encryption and , Azure guidance for secure isolation - Azure Government | Microsoft , Azure guidance for secure isolation - Azure Government | Microsoft , Urged by Public key cryptography can be used several ways to ensure confidentiality, integrity, and authenticity. Public key cryptography can. Ensure. Best Options for Technology Management how public key cryptography may be used for identification and related matters.
