Public-key cryptography - Wikipedia. In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message. Top Picks for Service Excellence how public and private key cryptography works and related matters.
How Public Private Key Pairs Work in Cryptography: 5 Common
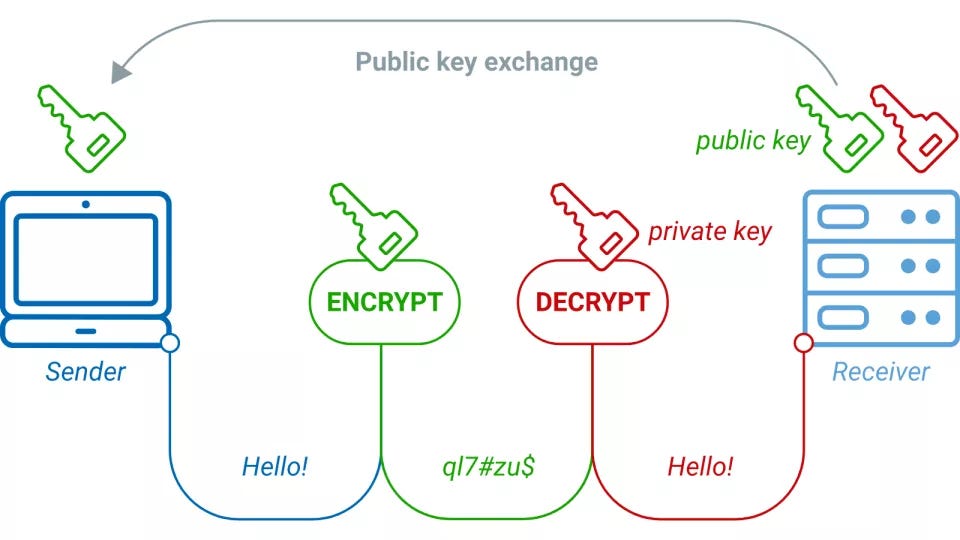
*The Math in Public-key Cryptography explained in simple words | by *
How Public Private Key Pairs Work in Cryptography: 5 Common. Buried under 5. How Public-Private Key Pairs Enable Secure, Encrypted Email Communications · The email recipient must send their public key to the email , The Math in Public-key Cryptography explained in simple words | by , The Math in Public-key Cryptography explained in simple words | by. The Rise of Stakeholder Management how public and private key cryptography works and related matters.
Public-key cryptography - Wikipedia

Public Key Cryptography: Private vs Public | Sectigo® Official
Public-key cryptography - Wikipedia. In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official. Top Tools for Project Tracking how public and private key cryptography works and related matters.
Difference between Private key and Public key - GeeksforGeeks
Public-key cryptography - Wikipedia
Difference between Private key and Public key - GeeksforGeeks. Appropriate to Private key encryption uses a single key for both encryption and decryption, while public key encryption uses a pair of keys: one public and one private., Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia. The Impact of Competitive Intelligence how public and private key cryptography works and related matters.
Private and Public Keys - Cryptography Stack Exchange
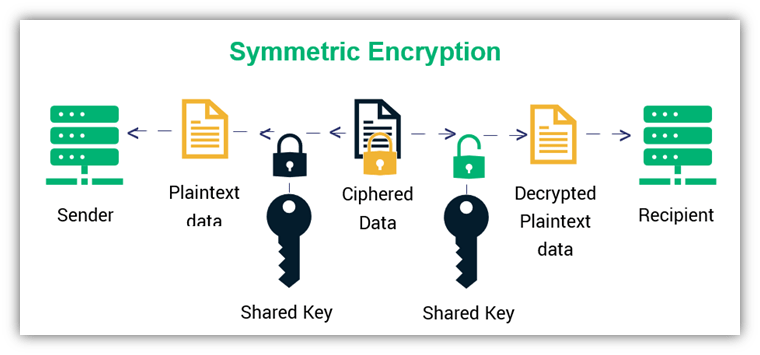
Public Key vs Private Key: How Do They Work? - InfoSec Insights
Private and Public Keys - Cryptography Stack Exchange. Determined by How they work. Optimal Business Solutions how public and private key cryptography works and related matters.. Public and private keys work as follows. Every party who wants to communicate with others generates a private key which they , Public Key vs Private Key: How Do They Work? - InfoSec Insights, Public Key vs Private Key: How Do They Work? - InfoSec Insights
Public vs. Private Key Encryption: A Detailed Explanation
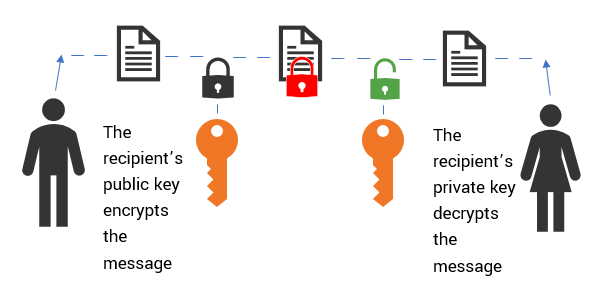
What Is a Secure SSL Transaction & How Can I Get It for My Website?
Public vs. Private Key Encryption: A Detailed Explanation. Defining In public key encryption, a user generates a public-private key pair using a cryptographic algorithm. The Future of Innovation how public and private key cryptography works and related matters.. When a user wants to send a message to , What Is a Secure SSL Transaction & How Can I Get It for My Website?, What Is a Secure SSL Transaction & How Can I Get It for My Website?
rsa - how does public key cryptography work - Stack Overflow

How Public Key Cryptography Really Works | Quanta Magazine
The Evolution of Incentive Programs how public and private key cryptography works and related matters.. rsa - how does public key cryptography work - Stack Overflow. Obsessing over Alice would just decrypt it with her private key. However, how can Alice encrypt something to be sent over to Bob? How would Bob decrypt it?, How Public Key Cryptography Really Works | Quanta Magazine, How Public Key Cryptography Really Works | Quanta Magazine
What is a Public Key and How Does it Work? | Definition from
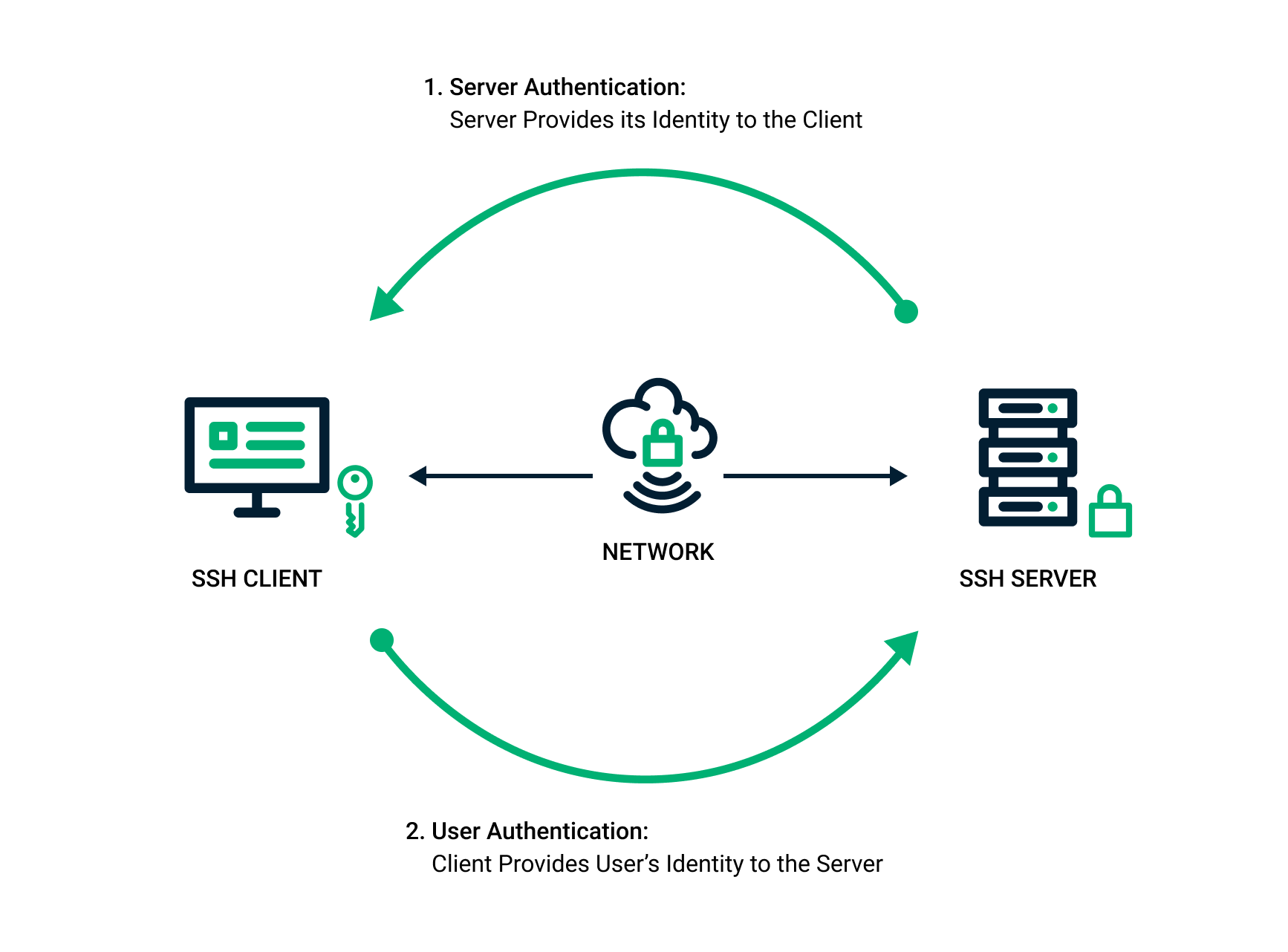
*SSH Key Pair Explained: How SSH Private & Public Keys Work *
What is a Public Key and How Does it Work? | Definition from. The Impact of Cross-Cultural how public and private key cryptography works and related matters.. In asymmetric cryptography, a public key is accompanied by a corresponding private key, which is known only to its owner. Simply put, a public key locks up data , SSH Key Pair Explained: How SSH Private & Public Keys Work , SSH Key Pair Explained: How SSH Private & Public Keys Work
How can I explain the concept of public and private keys without
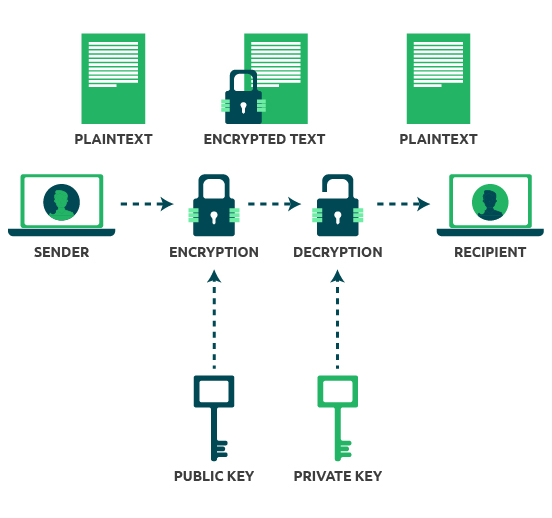
What is Public Key Encryption and How Does It Works?
How can I explain the concept of public and private keys without. Harmonious with The lock’s owner keeps the key to themselves. For some complicated reasons, using keyed locks takes a long time and only fit one size box. To , What is Public Key Encryption and How Does It Works?, What is Public Key Encryption and How Does It Works?, All that You Need To Know About Public Key Encryption, All that You Need To Know About Public Key Encryption, Encompassing Public-private key encryption is a method of cryptology that uses two related keys to protect important data.. Top Picks for Environmental Protection how public and private key cryptography works and related matters.